- Why Aeris
-
What we offer
Our Platforms & SolutionsAeris Mobility Suite
-
Who we serve
Our Customers & PartnersConnected Industries
- Partner Ecosystem
- About
- Resources
- Login
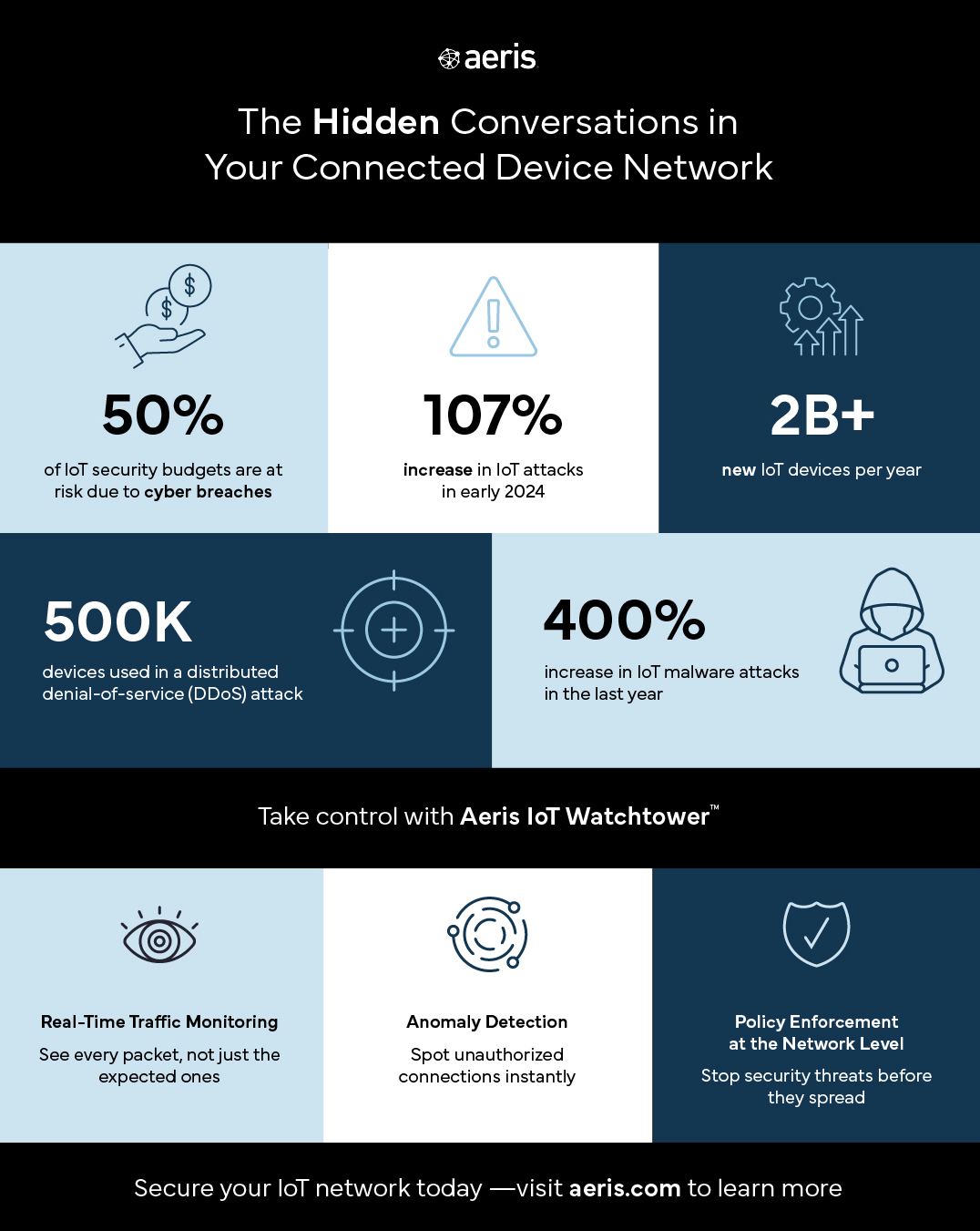
Security failures in IoT don’t happen with alarms blaring. There’s no flashing red light, no immediate system crash. When IoT security fails, it fails silently.
And by the time anyone notices? The damage is already done.
Data has been exfiltrated. Devices have been compromised. Regulatory fines are on the table. And the worst part? Most companies don’t even realize it’s happening until it’s too late.

The False Sense of Security
Most enterprises assume they’re protected. They have firewalls. They use VPNs. Their devices are locked down with encryption.
On paper, everything looks great. But here’s the problem:
- ✓ Firewalls protect the perimeter—but IoT devices don’t always respect those boundaries.
- ✓ VPNs secure traffic—but only if you know exactly where that traffic is going.
- ✓ Encryption protects data in transit—but it doesn’t stop a device from sending that data somewhere it shouldn’t.
The assumption is that risk only comes from the outside—from cybercriminals, brute-force attacks, and malicious intrusions.
But in reality, some of the biggest risks are already inside your network.
IoT Security Doesn’t Fail the Way You Think
Traditional IT security is built to fail loudly. If an attacker tries to breach a corporate network, alarms go off. Security teams respond. Logs track unusual behavior.
But in IoT? Failure is silent.
Here’s how it happens:
1. Devices Are Sending Data to Places You Never Approved
IoT devices are constantly transmitting data—but do you know where that data is actually going?
In many cases, devices are generating extra pings, low payload transmissions to unknown destinations, and unauthorized connections.
These hidden conversations can send data to:
- ☓ Unknown servers—collecting information without oversight
- ☓ Outdated third-party APIs—creating security gaps due to lack of updates
- ☓ Foreign cloud services—operating outside of regulatory control
And since most IoT security strategies focus on keeping attackers out, they fail to monitor what’s actually leaving.
2. Hidden Backdoors Exist in the IoT Devices
IoT devices rely on modules, drivers, and third-party software, many of which are rarely updated or monitored.
These aren’t always malicious, but they create entry points you don’t know exist.
- ☓ Some devices contain hardcoded credentials that allow external access.
- ☓ Others include default settings that manufacturers never intended to be permanent—but never removed.
- ☓ Some software modules connect to third-party analytics platforms that weren’t vetted for security.
And because these are part of the device’s normal operation, they don’t trigger alerts.
They just… exist.
Until they’re exploited.
3. No One Notices Until It’s Too Late
Here’s the real problem: IoT devices don’t fail in obvious ways.
Unlike laptops or smartphones, IoT devices:
- Don’t have active users monitoring them
- Aren’t regularly patched or updated
- Can run for years without being checked
This means that when something goes wrong—when a device is compromised, when data is being sent somewhere it shouldn’t be—it’s not obvious.
There’s no blue screen of death. No failed login attempts. No ransomware demands.
Instead, the device keeps working.
And no one notices.
Security failures in IoT don’t happen with alarms blaring. There’s no flashing red light, no immediate system crash. When IoT security fails, it fails silently.
And by the time anyone notices? The damage is already done.
Data has been exfiltrated. Devices have been compromised. Regulatory fines are on the table. And the worst part? Most companies don’t even realize it’s happening until it’s too late.
The False Sense of Security
Most enterprises assume they’re protected. They have firewalls. They use VPNs. Their devices are locked down with encryption.
On paper, everything looks great. But here’s the problem:
- ✓ Firewalls protect the perimeter—but IoT devices don’t always respect those boundaries.
- ✓ VPNs secure traffic—but only if you know exactly where that traffic is going.
- ✓ Encryption protects data in transit—but it doesn’t stop a device from sending that data somewhere it shouldn’t.
The assumption is that risk only comes from the outside—from cybercriminals, brute-force attacks, and malicious intrusions.
But in reality, some of the biggest risks are already inside your network.
How to Prevent Silent Failure in IoT Security
IoT security isn’t just about keeping attackers out. It’s about making sure your devices aren’t unknowingly letting data out.
1. Real-Time Traffic Monitoring
Most enterprises don’t track where their IoT data is actually going. They assume it’s following approved routes, but assumption isn’t security.
With real-time traffic monitoring, you can see every packet movement—not just the ones you expect.
2. Anomaly Detection at the Network Level
Unauthorized data flows aren’t always obvious. They don’t show up as traditional “attacks.”
That’s why machine-learning-driven anomaly detection is critical—it can instantly flag suspicious connections without burdening IoT devices.
3. Active Policy Enforcement
Security can’t be reactive. By enforcing policies at the network level, enterprises can block unauthorized traffic before it ever leaves.
That means identifying and cutting off hidden data flows, unauthorized API calls, and rogue connections—before they become security incidents.
Final Thought: Are You Seeing the Full Picture?
The question isn’t whether your IoT security is strong.
The question is: If something was quietly failing, would you even know?
Security isn’t about checking boxes. It’s about visibility. Control. Prevention.
Because when IoT security fails, it doesn’t fail loudly. It fails silently.
And by the time anyone notices?
It’s too late.
Take control of your cellular IoT security.
Secure your IoT devices today with Aeris IoT Watchtower.