- Why Aeris
-
What we offer
Our Platforms & SolutionsAeris Mobility Suite
-
Who we serve
Our Customers & PartnersConnected Industries
- Partner Ecosystem
- About
- Resources
- Login
The ability to deliver real-time, connected care—anytime, anywhere—is no longer a vision of the future; it’s happening now.
The biggest takeaway from HIMSS 2025 was that the technology innovation and adaptation continue to redefine patient care, with AI leading the charge.
AI was everywhere. It was part of the marketing taglines, almost every platform and product discussion, and in sessions. At times, it felt more like a buzzword than a breakthrough—more hype, less substance.
Yet beneath the AI fog, it was clear that the opportunities with AI in healthcare are massive. From enhancing patient care experiences to driving operational efficiency, AI is positioned to revolutionize the industry.
But amid all the AI excitement, one critical conversation was missing—connected care security beyond the walls of hospitals and care facilities.
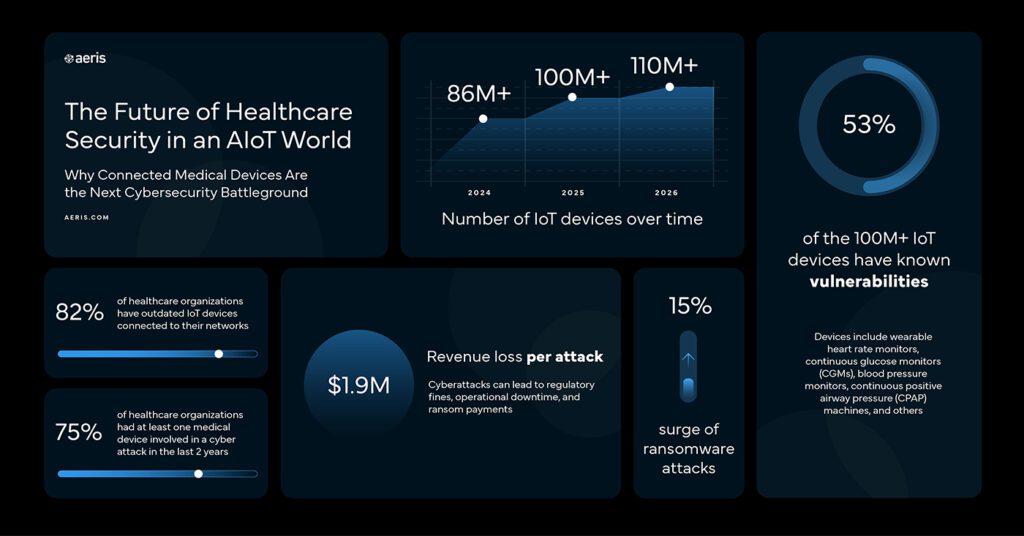
As patients move, their data moves with them. But does security move with the patient? How do care providers, device manufacturer, application developers, and patients themselves ensure that connected care remains secure beyond the perimeter of the care facilities? What role does each stakeholder plays? And what value can they create by enabling security into every layer of patient care?
Addressing these questions isn’t just about mitigating risk—it’s about ensuring that as healthcare technology advances, security keeps pace. The stakes are high, and the industry must act now.
Here are three key observations on what’s missing and what needs to change.
1. Reassess Security
Devices like respiratory monitors and glucose sensors have become essential part of patient care, which requires reassessment of security strategies.
According to the Berg Insights, there were just over 86 million connected healthcare devices deployed globally in 2024, with that number expected to approach 100 million by the end of 2025.
These devices enhance patient care and introduce cybersecurity concerns, according to an article in the Financial Times, emphasizing the need for robust security measures as these devices become more prevalent in our daily life, outside of the traditional care facilities.
2. Go Beyond Encryption
A common misconception in the industry is that encryption and compliance alone are enough to secure healthcare solutions.
This is a false sense of security.
Encryption does not prevent data from flowing to unauthorized or malicious servers. There is a high chance for data leak and potential exposure if the data outflow from devices cannot be reconciled to the data inflow into application servers.
What majority of solution providers lack are the abilities to:
- Know where every packet is going
- Ensure that the data only reaches authorized endpoints
- Identify anomalies before in traffic patterns before vulnerabilities they become breaches
3. Address the Overlooked Security Frontier: Patient Smartphones
Building connected health solutions that rely on smartphones has become easier and faster than ever.
Smartphones for such solutions serve as a conduit between medical devices and healthcare providers applications, transmitting sensitive health data through mobile apps.
But here lies the problem. While app-based solutions accelerate time-to-market, they also introduce security vulnerabilities that the solution provider cannot see.
It’s like driving down an open road on a clear sunny day in a car with an obscured windshield with no clear visibility into what lies ahead.
The patient data traveling from the device to the smartphone, and across the public networks becomes vulnerable to malware and rouge apps, unsecured Wi-Fi connections, and man-in-the-middle attacks.
From security perspective, patient smartphones as part of the connected solution aren’t just a convenience—they’re a major security blind spot that needs to be addressed.
Final Thought
AI is poised to transform remote healthcare. The real-time continuous care will be on the move with the patients—young and old—wherever they go.
But as healthcare becomes more mobile and interconnected, security cannot be an afterthought.
To paraphrase a famous professor, the dark arts are many, varied, and ever-changing. The same holds true for cyber threats. The very AI-driven innovations that empower providers and patients can also be exploited be bad actors.


