While well-planned and well-managed IoT deployments are often a smart business decision, IoT devices have some unique vulnerabilities due to their limited memory and processing power, long life cycles, and the growing scale of deployments.
In recent years, the frequency of IoT breaches has increased exponentially. Consider what we know about the state of IoT security in 2021:
- 76% of IoT communications are insecure (1)
- the average cost of an IoT device attack is $4,200,000(2)
- the average amount of time to the first attack of an IoT device is five minutes (3)
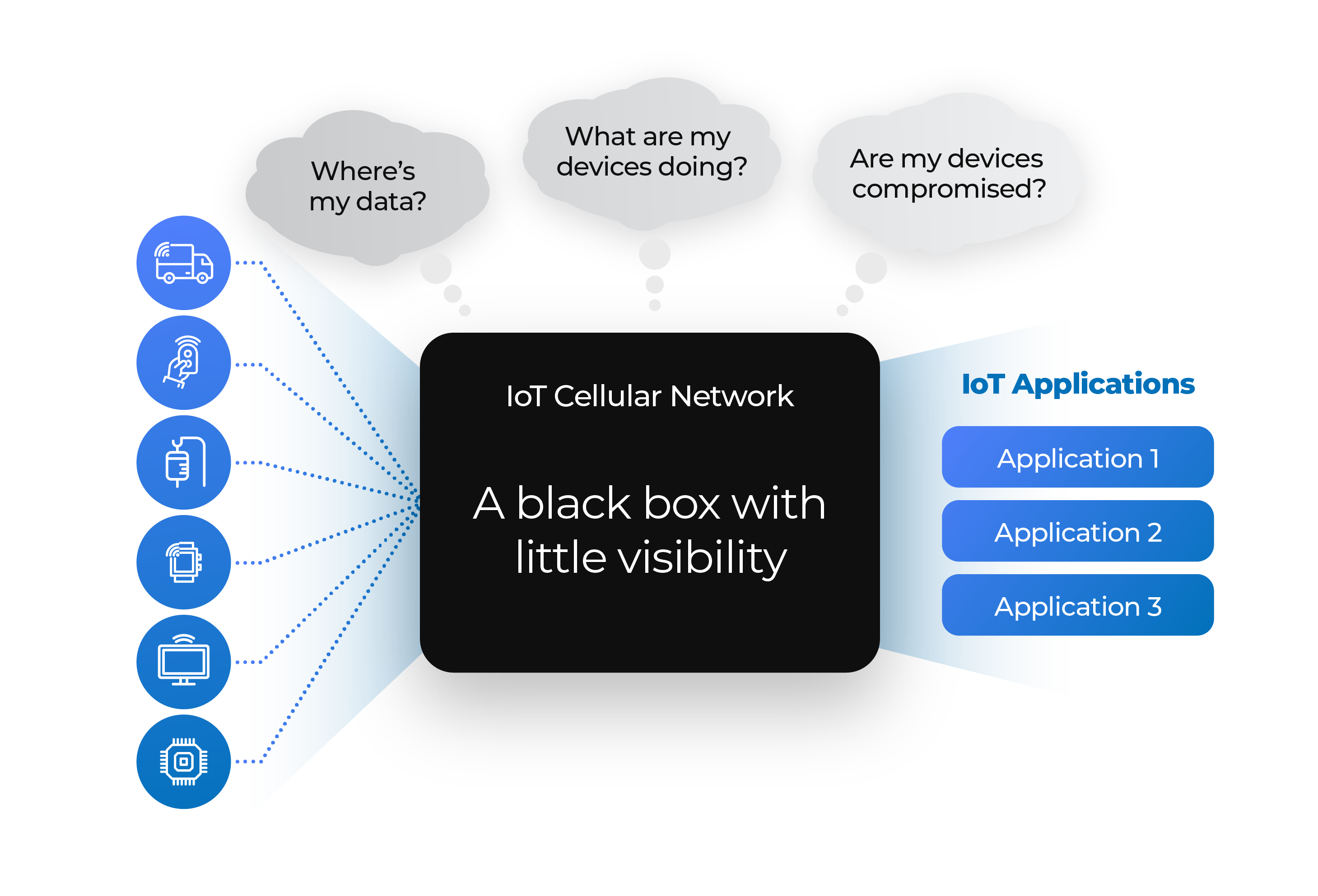
You Can’t Protect What You Can’t See
Visibility is critical to minimizing threat vectors as the threat surface for IoT devices expands. For instance, back in 2015 Fiat Chrysler had to recall 1.5 million cellularly connected vehicles including Jeep Cherokees, Jeep Grand Cherokees, Dodge Vipers, Dodge Challengers, and several other models because of a software bug. (4)
Researchers discovered that they could exploit the bug to hijack a Jeep, not only controlling every single component of the car and commanding it to do whatever they wanted but also gaining access to Fiat Chrysler’s entire deployment of connected vehicles.
Why do companies like Fiat Chrysler overlook these kinds of flaws? Some assume that their deployments are already secure simply because their devices were designed to be “secure.” The misconception here is that security only exists at the device level, but this idea leaves major openings at the network (and in the case of Fiat Chrysler) the application layer as well.
Other barriers to visibility that could result in breaches include:
- Emphasis on preventing breaches while neglecting detection and response
- Lack of expertise or personnel available to effectively monitor or enforce the security posture
- Legacy devices are incapable of software updates and integrations necessary for full visibility and latest security standards
- The number of IoT devices far outweigh the number of computers and personnel assigned to monitor them
- Non-IoT security solutions (typically designed for IT) are often bolt-on and cannot provide visibility at scale
- Many IoT products cannot be designed for, or tested against, all potential exploitations of unknown vulnerabilities arising from different deployments, environments, and locations
These gaps in IoT security visibility prevent timely detection of malicious activity and data exfiltration while also jeopardizing compliance with certain industry regulations like Personal Identifiable Information (PII), Payment Card Industry Data Security Standard (PCI), and the Health Insurance Portability and Accountability Act of 1996 (HIPAA).
How Intelligent IoT Security Keeps Watch Over IoT Deployments
Next-generation, purpose-built IoT security solutions are designed to provide continuous operational behavior visibility and analytics. By leveraging advanced machine learning capabilities and algorithms, enterprises become empowered to prevent, detect, and respond to the evolving cybersecurity threatscape.
Aeris’ real-time network visibility and machine learning capabilities deliver three key immediate benefits:
- Continuous monitoring of IoT network activity that complements and strengthens existing security strategies
- Rapid detection and remediation of security incidents tracked and managed through a user-friendly dashboard that visualizes indicators of compromise (IoCs), deep forensics, actionable alerts, and immediate response
- Compliance with standards and best practices thanks to risk-scoring algorithms that are dynamically updated to reflect the growing cybersecurity attack surface in real time
Intelligent IoT Security Brought to You By Aeris
Ready to check out the next-generation of purpose-built IoT security solutions? Contact one of our solutions architects to learn more about the Aeris Intelligent Security Center.
You can also join our webinar on November 16th, Implementing Security Management Best Practices, to learn the best practices for cellular IoT connectivity and see a preview of the Aeris Intelligent Security Center.
We look forward to seeing you there!