Embracing the Role of IoT Security in Your Business Strategy
Internet of Things (IoT) security breaches are skyrocketing. According to a 2021 Kaspersky security report, around 1.51 billion breaches of IoT devices took place from January to June of 2021, an increase from 639 million from January to June of 2020. The rest of 2021 shows no signs of IoT breaches slowing down. According to a third quarter data breach analysis report from the Identity Theft Resource Center (ITRC), the U.S. is on pace to set the all-time record for data breaches well before the end of the year.
With the proliferation of IoT security breaches, how have companies altered their perception and approach toward implementing a secure IoT strategy?
Survey Says
Last month, our CTO Syed “Z” Hosain presented an IoT World webinar titled Overcoming the Cellular IoT Connectivity Challenge: How to Deliver Scalable and Secure IoT.
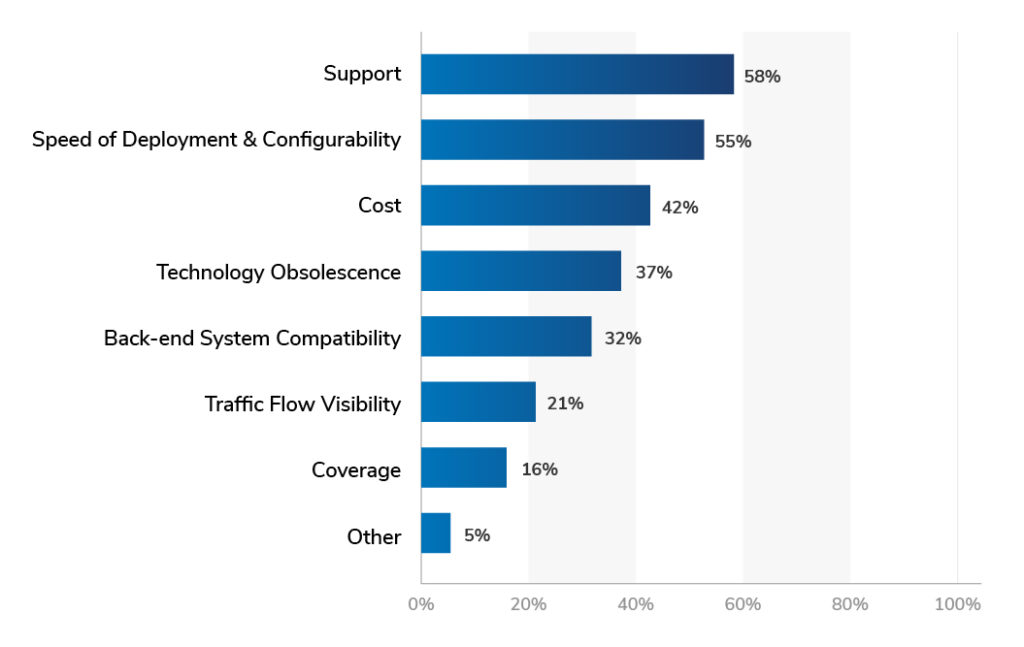
One of the survey questions he asked the audience was “Which of the following criteria do you think are most important for your IoT strategy?”
These were the results:
While we didn’t explicitly list “Security” as an option, we noticed that no one offered it as a criteria by selecting “Other.” Some of the people who answered this question may also have been thinking of security when they answered “Traffic flow visibility.” However, the results suggest that security is not considered a major criteria for a business’ IoT strategy.
Why IoT Security is Often an Afterthought
Leaders tend to prioritize investments that have exciting near-term payoffs such as cost, speed, and timely support. Even in our personal lives, we tend to get more excited about buying a big ticket item like a new house than we do about paying for the insurance, but it would be careless to make a big investment without paying the extra price to minimize and mitigate risk.
The same is true of IoT security.
IoT can be a very promising investment when it comes to enhancing efficiencies, growth, and profitability. Although many IoT investment plans consider ways to mitigate financial risks, security risks are often an afterthought. Before investing in an IoT deployment, how many companies or product managers consider the quantitative and qualitative impact of something as benign as traffic anomalies, or something as impactful as a security breach?
IoT deployments can lead to long-lasting growth and profitability, but left unchecked, they can become a growing, standing security risk that costs your company rather than benefiting it.
Security breaches often cost millions of dollars, and the pressure is on for Chief Intelligence Security Officers (CISOs) to prevent and contain them. Fortunately, there are steps that can be taken to detect and minimize the impact.
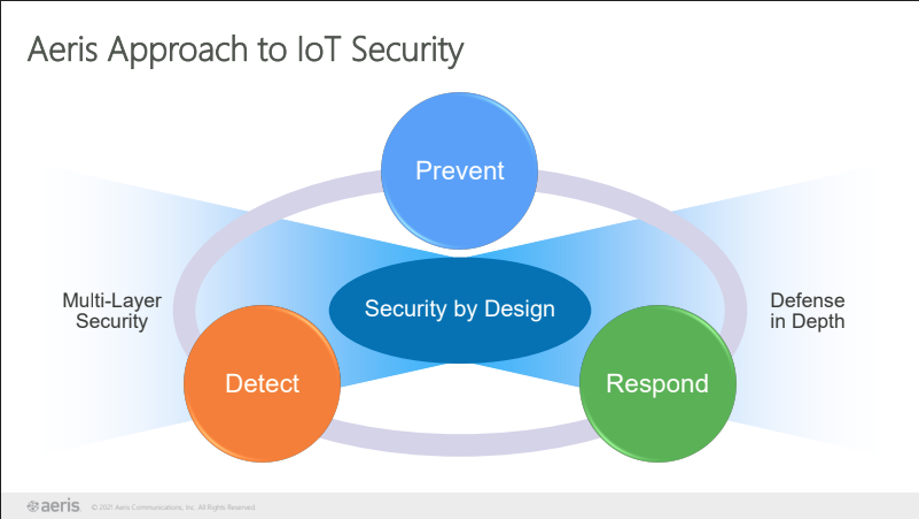
Security by Design: Prevent, Detect, and Respond
With the Aeris IoT Connectivity Platform, you can gain deep insights and advanced network intelligence across all devices to prevent, detect, and respond to anomalies and potential breaches. Aeris owns and maintains core network equipment that supports cellular connectivity for millions of IoT devices around the world. As soon as a threat or weakness is detected, our intelligent network can make immediate recommendations for actions to avoid costly attacks.
Aeris Security Management features include device/account lockout and virtual private networks (VPNs), whitelisting devices, role-based access control, operational behavior visibility and analytics, and anomalous new endpoint alerts and reports. We will also introduce new features over the next few quarters that leverage advanced algorithms to enable rapid detection of anomalies and security incidents.
Stay Ahead of IoT Security with Aeris
Want to know how to strengthen the security of your IoT deployment? Download the recording of our latest webinar.
Looking for a connectivity partner that can better secure your IoT deployment? Contact the Aeris Global Sales Support team for a consultation.